At this point your integration almost works. Your AD FS server knows what Papyrs expects, and Papyrs knows what your AD FS server expects. Now you have to decide which AD properties to send to Papyrs at sign on.
Open the AD FS Management tool select and Edit Claim Issuance Policy for your Papyrs 3rd party trust connector.
Two claims rules are needed, the third one is optional. Click on
Add Rule...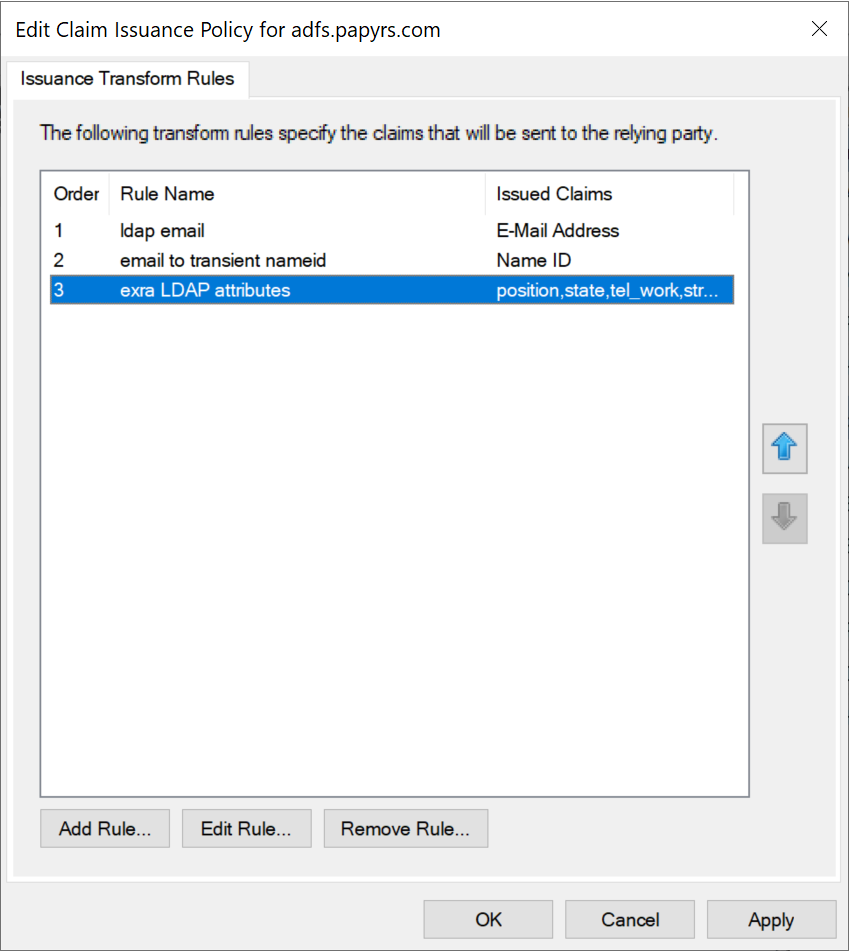
In the first step of the wizard choose "Send LDAP Attributes as Claims" and click Next. Configure the claim rule to map LDAP Attribute E-Mail-Addresses to outgoing Claim Type E-Mail Address. See screenshot:
The purpose of this rule is to share the AD user's email address with Papyrs during login. Papyrs identifies users by email address.
Then create a second Claim Issuance Policy. This time choose Transform an Incoming Claim in the first page of the wizard. Here we want to map the incoming claim type E-Mail Address (unspecified) to Name ID (Transient Identifier). The other defaults are fine, see screenshot:
The purpose of this rule is to let AD FS know that the users are identified by their email address. The order of the claims matters.
(optional) If you want to share additional AD properties with Papyrs at sign on you can do that by creating a 3rd rule.
Optional LDAP attributes to sync with Papyrs profiles during login:
- website
- twitter
- tel_home, tel_work, tel_mobile
- position
- street
- city
- street
- state
- zipcode
- country
- bio
- birthday
If you have custom attributes in your Papyrs people directory we can sync those as well. Please contact us at
team@papyrs.com and we'll set sync rules up for you.


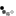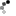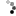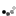 Loading...
Loading...
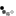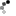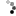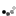 Loading...
Loading...
 Uploading...
Uploading...